If you have ever poked around in your network settings or set up a VPN manually, you have probably stumbled across a confusing alphabet soup of acronyms. One of the most common pairings you will see is L2TP/IPsec. While it sounds like a complex robot name, it is actually a standard way computers talk to each other securely.
Although modern VPN services are moving toward newer technologies, understanding L2TP/IPsec is still useful for knowing how your data stays safe—or why your internet might be running a bit slow. Let’s break down exactly what this protocol is, how the two parts work together, and whether you should actually be using it today.
The Dynamic Duo: What is L2TP/IPsec?
To understand this term, we have to split it in half because it is actually two different protocols working in tandem. L2TP stands for Layer 2 Tunneling Protocol. It was first proposed back in 1999 as an upgrade to older technologies like L2F and PPTP (Point-to-Point Tunneling Protocol) .
Here is the catch: L2TP by itself is surprisingly vulnerable. It is great at creating a “tunnel” for your data to travel through, but it does not provide strong encryption or authentication on its own . If you used L2TP alone, it would be like sending a letter in a clear plastic envelope—people can see it is a letter, but they can also read what is inside.
This is where IPsec (Internet Protocol security) comes to the rescue. IPsec is a flexible protocol designed for end-to-end security that authenticates and encrypts every single IP packet in a communication . When you combine them, L2TP builds the tunnel, and IPsec locks it down with military-grade encryption . This combination is widely adopted because it provides confidentiality, integrity, and authentication for your data .
How Does It Work? (The “Double Wrapping” Effect)
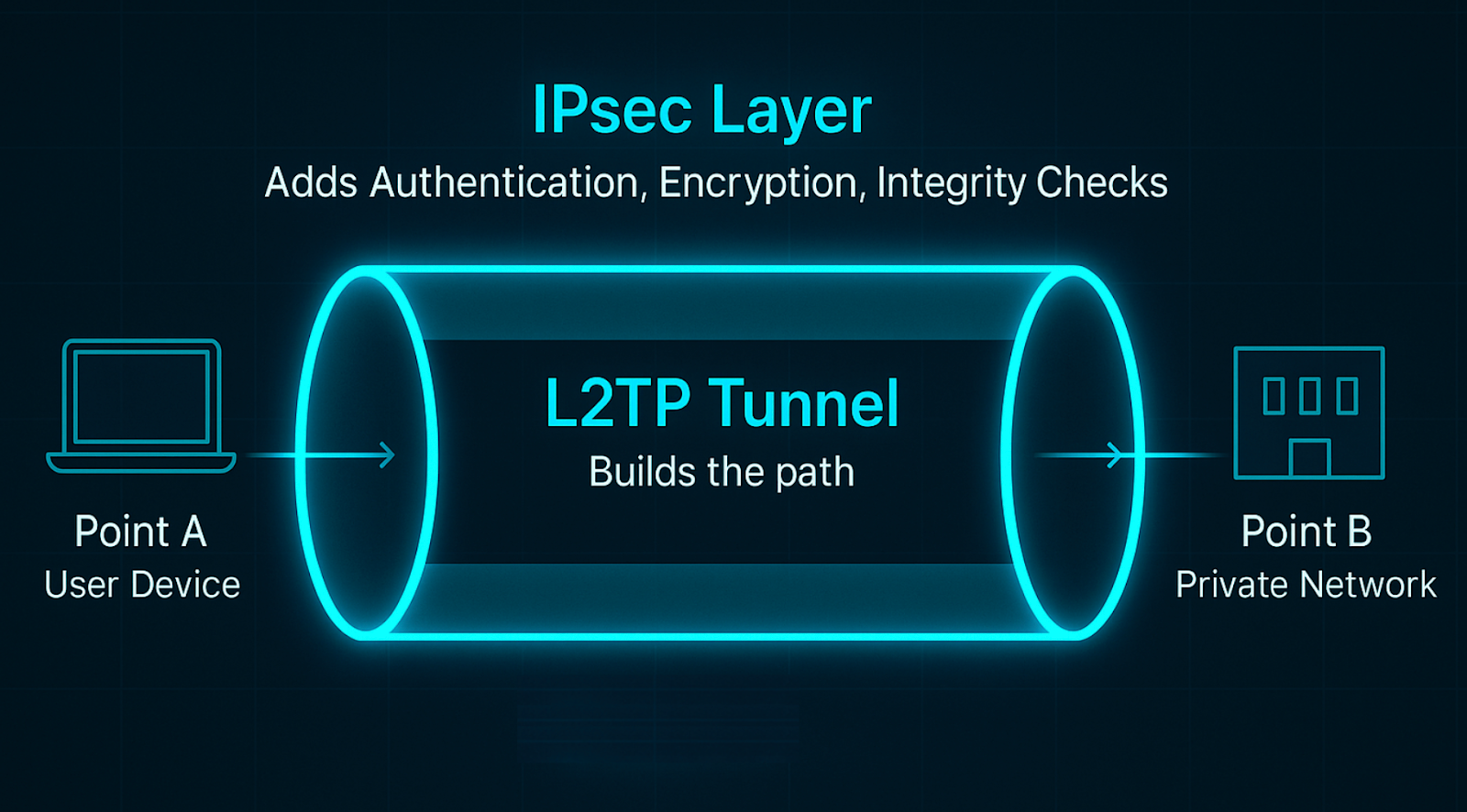
Imagine you are shipping a fragile package. First, you put the item in a box (L2TP). Then, to make sure it is absolutely safe, you put that box inside a heavy-duty, locked steel container (IPsec). In technical terms, this is called encapsulation.
L2TP creates a tunnel between the client (your computer) and the VPN server. It initiates the connection using components called the Access Concentrator (LAC) and the Network Server (LNS) . However, because L2TP does not encrypt the data, IPsec steps in to wrap that data in a layer of encryption—often using strong standards like AES-256 .
While this makes your connection secure, this “double encapsulation” process creates a significant downside: it creates overhead. Because the computer has to work twice as hard to package and unpackage the data, L2TP/IPsec can sometimes be slower than other protocols .
The Pros and Cons of Using L2TP/IPsec
Like any technology, L2TP/IPsec has its strengths and weaknesses. It was the industry standard for a long time, but newer protocols are starting to leave it behind.
The Advantages
For years, this protocol was the go-to choice for enterprise networks and personal VPNs for a few key reasons:
- Better Security than PPTP: It is a massive step up from the obsolete PPTP protocol, offering actual data integrity and confidentiality .
- High Compatibility: Because it has been around since the 90s, almost every modern device—from Windows and Mac to Android and iOS—has built-in support for it .
- Data Integrity: The IPsec layer prevents data from being tampered with while it is in transit .
The Disadvantages
Despite its popularity, there are significant reasons why top-tier VPN providers like ExpressVPN have moved away from supporting it in their apps .
- Slower Speeds: As mentioned earlier, the double encapsulation process requires more processing power, which can slow down your internet connection compared to lighter protocols like OpenVPN .
- Firewall Headaches: L2TP uses specific UDP ports (usually port 500 for the key exchange and 1701 for the tunnel) . These ports are easily identified and frequently blocked by firewalls. If you are trying to use a VPN at a strict office or in a country with heavy censorship, L2TP/IPsec is often the first thing to get blocked .
- Setup Complexity: While supported by many devices, setting it up manually can be tricky compared to just clicking “connect” on an app, and configuration errors can leave you vulnerable .
| Category | Pros (Advantages) | Cons (Disadvantages) |
|---|---|---|
| Security | Better than PPTP: It offers a significant security upgrade over the obsolete PPTP protocol, providing data confidentiality, integrity, and authentication . Strong Encryption: When paired with IPsec, it utilizes robust encryption standards like AES-256 to protect data in transit . |
Moderate Security Level: It is considered only “moderately secure” compared to modern gold standards like OpenVPN or Lightway . Configuration Risks: Security relies heavily on correct configuration; weak pre-shared keys or setup errors can leave the connection vulnerable . |
| Compatibility | Highly Compatible: It is supported natively by almost all major operating systems (Windows, macOS, iOS, Android) and devices, requiring no extra software installation . Multi-Protocol Support: capable of encapsulating different network protocols, making it versatile for various network environments . |
Complex Setup: Unlike modern “one-click” VPN apps, setting up L2TP/IPsec manually can be tricky and cumbersome for average users . |
| Performance | Stable Connection: It is generally a stable and functional choice for enterprise VPNs and remote access . | Slower Speeds: The “double encapsulation” process (L2TP tunnel + IPsec encryption) creates data overhead, which can significantly slow down internet speeds compared to lighter protocols like OpenVPN . |
| Connectivity | Standard Usage: Useful for basic anonymization and accessing standard corporate networks . | Firewall Issues: It uses fixed UDP ports (typically port 500 and 1701), which makes it easy for firewalls and NAT devices to detect and block the connection . |
L2TP vs. The Competition: How Does It Stack Up?
In the world of VPNs, L2TP is essentially the middle child—more secure than the old stuff, but not as fast or agile as the new stuff.
- L2TP vs. PPTP: This is an easy win for L2TP. PPTP is fast but incredibly insecure and obsolete. L2TP/IPsec is much safer .
- L2TP vs. OpenVPN: OpenVPN is generally considered the gold standard. It offers better security and is much better at bypassing firewalls because it can run on any port. L2TP is often slower and easier to block .
- L2TP vs. Lightway: Modern protocols like ExpressVPN’s Lightway are built from the ground up to be faster, more reliable, and just as secure, leaving older protocols like L2TP in the dust regarding performance .
Conclusion: Should You Use It?
L2TP/IPsec is a reliable, “workhorse” protocol that played a huge role in the history of internet privacy. It is certainly secure enough for general browsing if you have no other options. However, due to its speed limitations and the fact that it is easily blocked by firewalls, it is rarely the best choice today.
If you have the option, modern VPN apps will usually steer you toward better protocols like Lightway or OpenVPN automatically . But if you are on a legacy device or a restrictive corporate network that specifically requires it, L2TP/IPsec remains a functional, if slightly dated, way to keep your data under wraps.


